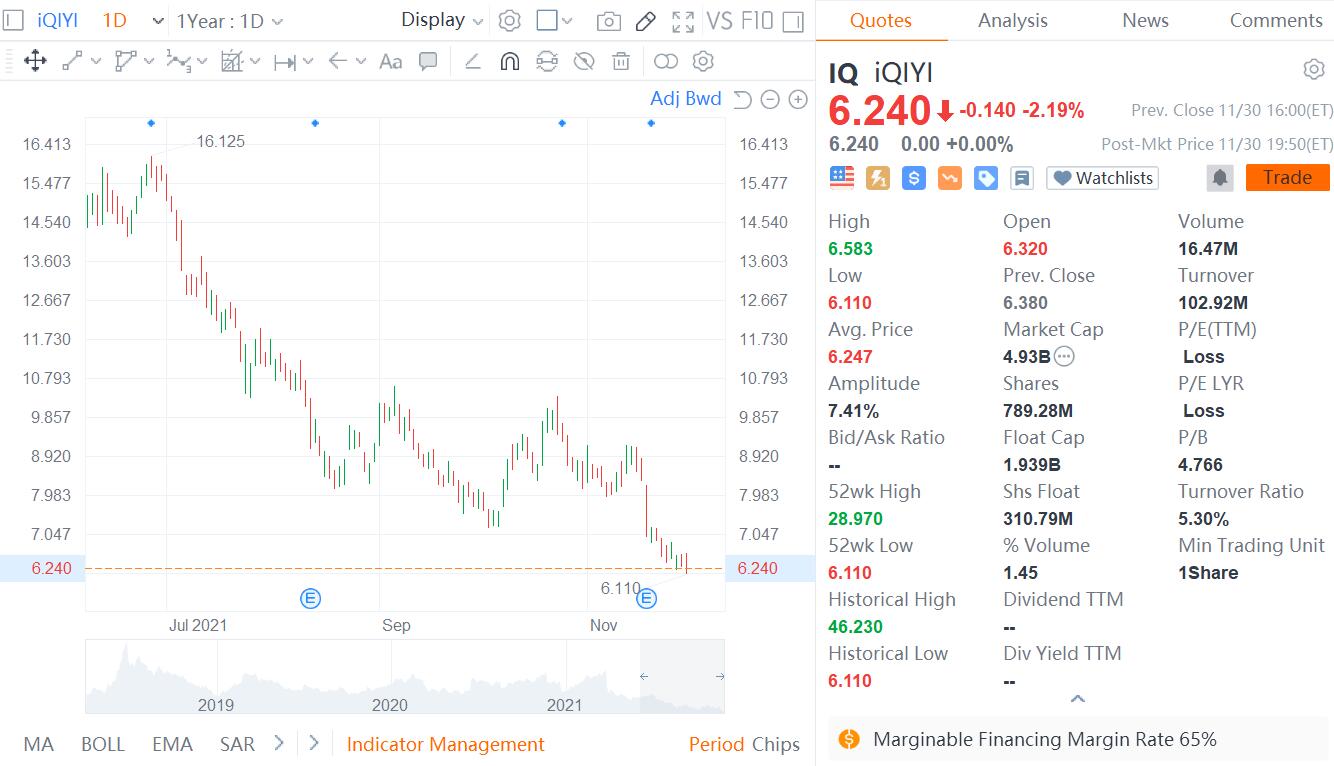
On April 8, Chinese web security firm Huorong Security confirmed that the suspected sample of WannaRen ransomware shares on the Internet was actually a virus decryption tool. The team then conducted traceability analysis on the real virus samples, and captured its propagation script (currently deleted by the author).
Through further tracing, Huorong Security discovered that the virus propagation script carried by a maliciously tampered open source code editor on the website named Xixi Software Center (www.cr173.com) has homology with the ransomware virus transmission script. Therefore, it is not excluded that the download site was once used as one of the channels for the spread of WannaRen ransomware.

The ransomware captured by Huorong Security will execute the two commands of downloading mining virus and ransomware at the same time locally, and can also be spread through the "eternal blue" vulnerability, and uses the asymmetric encryption method like most ransomware viruses. Therefore, it cannot be decrypted for now.
The virus propagation script carried on the Xixi Software website currently only spreads mining viruses, but it does not rule out the possibility of spreading ransomware in the future.
What is worrying is that through the search, the download station's open source code editor ranks first among similar software (as shown below), which may have affected many users.

Currently, the Huorong Security software (personal version and enterprise version) has defended and intercepted the ransomware virus and its transmission scripts in virus detection, system reinforcement, behavior defense, and firewall.

In fact, in order to obtain traffic benefits, various download sites on the Internet have long become a gathering place for viruses and rogue software. Huorong Security has repeatedly disclosed the chaotic phenomenon of the download station. In order to avoid the above-mentioned viruses and other hazards, everyone must go to their official website when downloading the software.
Here is the full analysis report from Huorong:
1. Detailed analysis
Virus spread
The WannaRen ransomware that has spread in large numbers recently is mainly distributed through the "hidden" virus transmission script. Malicious script, as shown below:
Malicious script content
After the virus script is executed, it will download and execute multiple malicious modules, including: ransomware, mining virus, eternal blue vulnerability attack tool. Among them, the eternal blue vulnerability attack module will spread malicious code in the network through a vulnerability attack.
After the attack is successful, a remote malicious script (my ****. At.ua/vip.txt) will be run in the attacked terminal. This script reports that the logic of the above vip.txt malicious script module is basically the same, which is also downloaded Many of the above malicious modules also do not rule out the possibility of the malicious script downloading and executing the WannaRen ransomware virus. The content of the script is shown below:
Malicious script content (my ****. At.ua/vip.txt)
2. Ransomware virus
The ransomware code is called in the form of "white plus black". The hidden virus spread script will download the "white plus black" malicious modules (wwlib.dll and WinWord.exe) to the c: \ ProgrAMData directory for execution. After the virus runs, it will register C: \ ProgramData \ WinWord.exe as a system service, and the computer will execute malicious code and encrypt user files after the computer restarts.
As shown below:
"White plus black" malicious module
Virus service
After restarting, the virus code will start the system program (svchost.exe, cmd.exe, mmc.exe, etc.) to inject the ransomware virus code into the started system process. Relevant behavior phenomena, as shown in the following figure:
Ransomware behavior
The ransomware uses symmetric and asymmetric (RSA + RC4) encryption. Unless the private key of the ransomware author is obtained, it cannot be decrypted. Ransomware first generates a random RC4 key, such as "p2O6111983YU1L", and uses this single key to encrypt all files. The encrypted files will be added with the .WannaRen suffix.
After generating the key, the virus will import the RSA public key to encrypt the randomly generated RC4 key and store it at the head of each encrypted file. The specific code is shown below:
Generate random RC4 key
Import public key encryption RC4 key
Virus author's public key
Use RC4 algorithm to encrypt the original file
In order to allow the ransomware computer to continue to be used, the ransomware virus will skip the special path when encrypting, and the skipped path keyword is as shown in the following figure:
Skipped path keywords
The ransomware will encrypt files with specific extensions. The specific file types are shown in the following figure:
Encrypted file extension
The encrypted file is composed of two parts, the front is the encrypted RC4 key, and the back is the encrypted file content. The specific code is shown below:
Write encrypted files
An example of the encrypted file is shown below:
Encrypted sample file content
The ransomware will release the ransomware document when encrypting each folder, and after completion, it will create "Please decrypt this text.gif", "Please decrypt this text.txt" and a decryption program on the public desktop. @ WannaRen @ .exe ".
The specific code is shown below:
Release Ransomware Instructions and Decryption Procedure
The ransomware decryption tool and ransomware letter are shown below:
Ransomware decryption tool
Extortion letter
2. Traceability analysis
Through the traceability analysis of the script data related to the "WannaRen" ransomware virus, we found that the software in the download station platform "Xixi Software Center" (www.cr173.com) also has a similar malicious script propagation process.
For example, the "Notepad ++" software downloaded from the "Xixi Software Center" carries script code similar to the ransomware transmission process. The relevant page of the download station is shown below:
Xixi Software Center related download page
When the software download is complete, the malicious powershell code is hidden in it, and the relevant code data is shown in the following figure:
Malicious powershell script code
By decrypting this powershell code, it was found that it will eventually download and execute the malicious script in "http://cpu.sslsngyl90.com/vip.txt".
Comparing this malicious script with the ransomware virus script we obtained before, it is found that except for the "WannaRen" ransomware-related modules, the remaining malicious code is basically the same.
Malicious script code comparison
In summary, we do not rule out that the download site was once used as a channel for WananRen ransomware.
3. Appendix
Sample hash